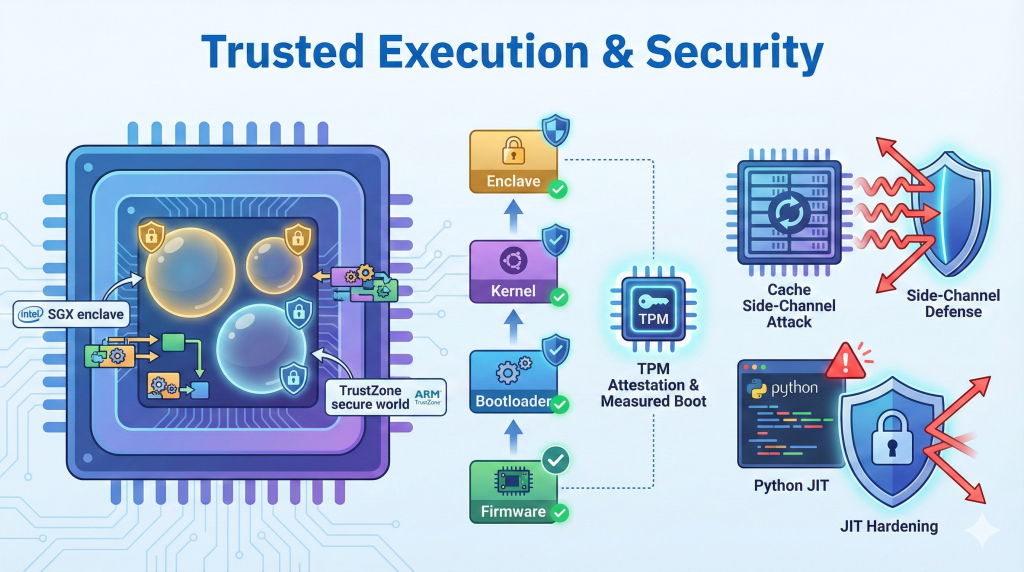
We study trusted execution and system security from hardware up to the OS and runtime layer. Our work uses Intel SGX and ARM TrustZone to build trusted execution environments (TEEs) that still work in realistic cloud and mobile settings — for example, migrating enclaves and SGX‑enabled VMs between hosts while preserving integrity and attestation, comparing SGX/TrustZone designs, and hardening secure boot flows so that kernels and bootloaders can be measured and verified end‑to‑end.
On top of these TEEs, we analyze and mitigate realistic attack surfaces: cache‑based side channels that recover Android pattern locks, weaknesses in kernel and Nested Kernel memory protection, and exploitation paths in copy‑and‑patch Python JIT engines. We also design secure ML runtimes (e.g., SGX‑based secure TensorFlow) that keep training and inference data confidential. The common theme is to make trusted execution practical and robust—by combining hardware enclaves, secure boot, and runtime hardening into one coherent security stack.